As smart grid tech is rolled out around the world to modernize legacy assets and integrate renewable energy generation, it is also making the...
Vous n'êtes pas connecté
- English
- Français
- عربي
- Español
- Deutsch
- Português
- русский язык
- Català
- Italiano
- Nederlands, Vlaams
- Norsk
- فارسی
- বাংলা
- اردو
- Azərbaycan dili
- Bahasa Indonesia
- Հայերեն
- Ελληνικά
- Bosanski jezik
- українська мова
- Íslenska
- Türkmen, Түркмен
- Türkçe
- Shqip
- Eesti keel
- magyar
- Қазақ тілі
- Kalaallisut ; kalaallit oqaasii
- Lietuvių kalba
- Latviešu valoda
- македонски јазик
- Монгол
- Bahasa Melayu ; بهاس ملايو
- ဗမာစာ
- Slovenščina
- тоҷикӣ ; toğikī ; تاجیکی
- ไทย
- O'zbek ; Ўзбек ; أۇزبېك
- Tiếng Việt
- ភាសាខ្មែរ
- རྫོང་ཁ
- Soomaaliga ; af Soomaali
Rubriques :
 Maroc - ITSECURITYNEWS.INFO - A La Une - 10/09/2024 10:32
Maroc - ITSECURITYNEWS.INFO - A La Une - 10/09/2024 10:32
Researchers Details Attacks On Air-Gaps Computers To Steal Data
The air-gap data protection method isolates local networks from the internet to mitigate cyber threats and protect sensitive data, which is commonly used by organizations dealing with confidential information such as personal, financial, medical, legal, and biometric data. By eliminating…
Articles similaires
Poland Arrests Suspected Russian Hacker Targeting Local Organizations’ Networks
Polish authorities have made a significant move in their cybercrime enforcement efforts by detaining a Russian national suspected of conducting...
Poland Arrests Suspected Russian Hacker Targeting Local Organizations’ Networks
Polish authorities have made a significant move in their cybercrime enforcement efforts by detaining a Russian national suspected of conducting...
Water Saci Hackers Leveraging AI Tools to Attack WhatsApp Web Users
Cybercriminals targeting Brazilian users have aggressively escalated their tactics, launching a highly sophisticated campaign dubbed “Water Saci.”...
Water Saci Hackers Leveraging AI Tools to Attack WhatsApp Web Users
Cybercriminals targeting Brazilian users have aggressively escalated their tactics, launching a highly sophisticated campaign dubbed “Water Saci.”...
Secure BYOD in a World with Increasing Threats
Organizations juggle a tough balancing act: enabling employees to use personal devices while safeguarding sensitive data.
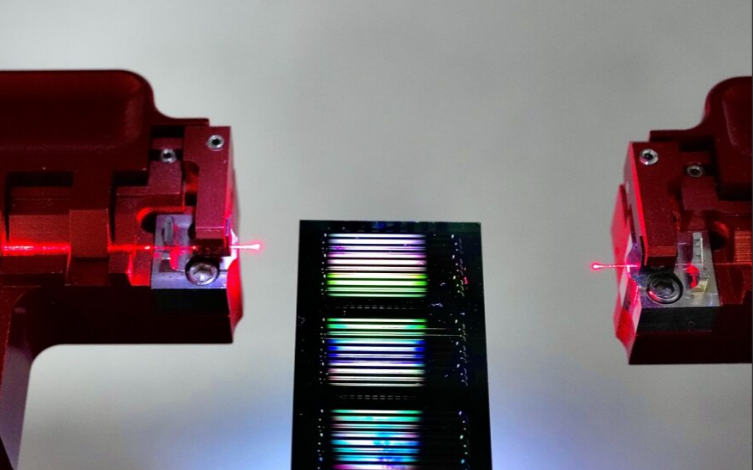
Sydney Team Blocks Noise in Chip-Scale Lasers
Insider Brief PRESS RELEASE — Researchers at the University of Sydney have cracked a long-standing problem in microchip-scale lasers by carving...
Sydney Team Blocks Noise in Chip-Scale Lasers
Insider Brief PRESS RELEASE — Researchers at the University of Sydney have cracked a long-standing problem in microchip-scale lasers by carving...
How Stablecoins Can Improve Payments And Global Finance – Analysis
Despite having a market capitalization of about 10 percent of Bitcoin, stablecoins are growing in influence because of the interconnections with...
The digital shield: How AI honeypots could protect Zimbabwe’s online future
Thabonga Masenda IN today’s connected world, cyber-attacks are no longer distant threats — they are right at our doorstep. From hackers stealing...
Les derniers communiqués
-
Star Alliance Named World’s Leading Airline Alliance Once Again
Deutsche Lufthansa AG - 08/12/2025
-
Adidas and arte antwerp launch first capsule collection, paying homage to north african football culture
Adidas - 05/12/2025
-
Adidas originals and willy chavarria release spring/summer 2026 collection & campaign
Adidas - 04/12/2025
-
adidas Originals, CLOT, and BAPE® Unite for Reimagined Superstar by Edison Chen
Adidas - 03/12/2025
-
Adidas basketball announces partnership with club 520
Adidas - 03/12/2025
-
Making invisible disabilities visible: Lufthansa joins the Hidden Disabilities Sunflower Program
Deutsche Lufthansa AG - 03/12/2025
-
More sustainable flying: Lufthansa Group further expands group-wide fuel efficiency program
Deutsche Lufthansa AG - 03/12/2025
-
Adidas re-defines game-changing control with launch of new PREDATOR
Adidas - 03/12/2025
-
Making invisible disabilities visible: Lufthansa joins the Hidden Disabilities Sunflower Program
Deutsche Lufthansa AG - 03/12/2025
-
Adidas unveils the new barricade – built on legacy, designed for control
Adidas - 02/12/2025